A JTAG/XSVF Library for Arduino
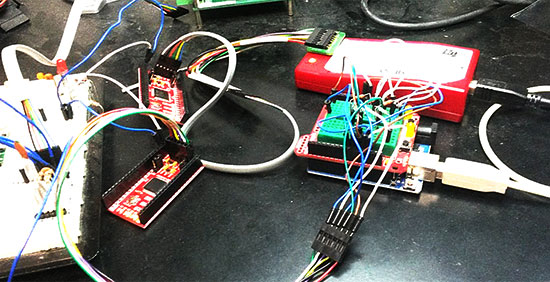
Marcelo Jimenez developed a library to use an Arduino as a JTAG programmer. Basically a Python script uploads a XSVF file to an Arduino which interprets it and performs the necessary JTAG manipulation in order to do the programming.
The project is pretty simple because it just uses a few resistors and some wires and the library is included in the Arduino library manager or you can check it on Github.
He also wrote an article to explain some JTAG, SVF and XSVF basics:
I have recently felt the need to incorporate a JTAG port in a project to program a hardware that contained a CPLD. The idea was to both program it and perform some integrity tests on the board. I imagined something using pogo pins, to make it easier and quicker to test everything. I would also write the necessary test routines and generate some kind of report.
With this objective in mind, I have decided to design an Arduino shield to do the job. The testing routines were not really a big deal. And I was sure I would find some JTAG library for Arduino ready to be used. That was not the case.
There were some projects using Arduino to control a JTAG TAP (Test Access Port), but they were all incomplete. And I had no idea what was really JTAG. So I had to study a little bit to make things work for me.
In the end, the challenge proved enlightening. There were some caveats, both from hardware and from software. I’ll try to address them in this article.