Developed on Hackaday: Mooltipass Arduino Shields Compatibility
Some of our dear readers may already have an infallible system to remember different complex passwords for the different websites they visit daily. This is why they may have not been following the offline password keeper that the Hackaday community is building.
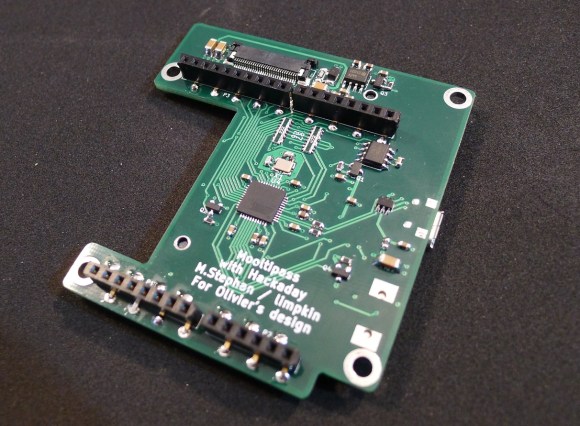
The Mooltipass has a characteristic that may regain their interest: it is possible to connect Arduino shields to it. In the video embedded below you can see the Arduino conversion process our development team imagined a few months back. The operation simply consists in using a knife to remove plastic bits on top of standard Arduino headers. We also embedded a few use cases with their respective sketches that may be downloaded from our official GitHub repository.
As with stacking several shields, a little tweaking may be required to keep the functionalities from both the Mooltipass and the connected shield. We therefore strongly welcome Arduino enthusiasts to let us know what they think of our setup.
In the meantime, you may want to subscribe to our official Google Group to stay informed of the Mooltipass launch date.
Filed under: Hackaday Columns